-
How To Install Switch On Pfsense
Welcome back to this series, in which we discuss and configure the various features of pfSense. In the last article, we set up a basic network where LAN users are automatically assigned IP address settings via DHCP and have access to the Internet via the default NAT rule on pfSense. In this article, we will look at configuring VLANs and also touch on firewall rules.
VLANs and Inter-VLAN routing
PfSense should work fine for VPN as you thought. So for two switch setup: Wan > pfSense > 2920 POE+ (layer 3) + 2530G 48 (or 2x A5120 24).
Depending on the hardware on which you install pfSense, you may be limited to a certain number of interfaces. For example, when we installed pfSense on VMware, we added only two network adapters – one for LAN and one for WAN. What if we wanted to have a dedicated interface for a DMZ? In our case, we could just add another network adapter but, on physical hardware, this may not be so simple. This is where VLANs and VLAN trunking come in.
If you are familiar with Cisco routers, you know the concept of Inter-VLAN routing, also known as routing on a stick. This feature allows us to configure the link between a router and a switch as a trunk link and then, on the router, we can configure sub-interfaces that belong to different VLANs.
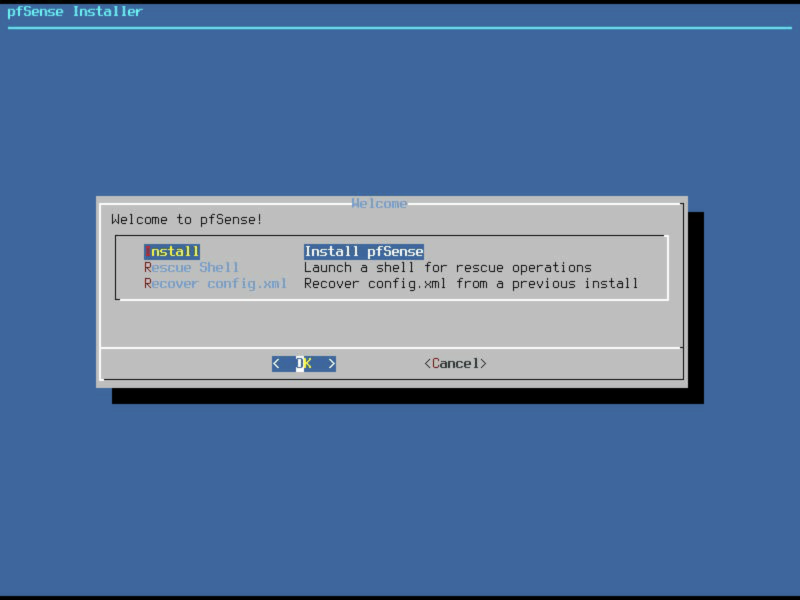
The same thing can be achieved on pfSense, where we can split an interface into several virtual interfaces that belong to different VLANs. Let’s use the diagram below for this article:
At the moment, we are accessing the webGUI of pfSense via its LAN interface. Since we will be editing this interface, let’s temporarily allow pfSense to be configured via its WAN interface so that we don’t lock ourselves out.
By default, the webGUI is not accessible from the WAN because all incoming connections on the WAN are denied by default. Therefore, we need to add a firewall rule on pfSense for this connection that says “allow IP address (on the WAN side) to open HTTP connection to the WAN interface IP.”
Note: If we were using HTTPS to connect to the webGUI, then we would allow HTTPS instead of HTTP.
To add this rule, we will navigate to Firewall > Rules and under the WAN tab, we will click the add new rule button. The settings on my own rule are as shown below:
Hint: The IP address of my host PC is 192.168.8.100 and I allowed only that IP address to access the webGUI from the WAN.
Once you are done, you can save your rule. Another thing to note in our lab environment is that our WAN interface is actually connected to a private IP address space network, i.e., 192.168.8.0/24. Therefore, we need to remove the default WAN rule that blocks connections from private networks:
If we click on the edit rule button, it will take us to the WAN interface settings page, where we just need to uncheck the box that says “Block private networks.”
Save your settings, apply your changes, and then confirm that you can reach the webGUI from the WAN interface:
As you can see in the screenshot above, I can now access pfSense via the WAN interface, so we can go ahead with our VLAN configuration. To configure VLANs, we navigate to Interfaces > (assign). This will give us access to several tabs, including the VLANs tab, which is where we need to add VLANs.
To add a VLAN, we will click on the button highlighted above, which will bring us to the VLAN edit page.
The Parent interface is the interface that we want to act as our trunk link. This should be the interface currently assigned to the LAN—in my case, its le0. The VLAN tag will be the VLAN number we want to assign. It should be the same as the one we will configure on the switch later. For this article, we will use VLAN 10 for the LAN and VLAN 20 for the DMZ. The Description field is an optional field to help you identify the purpose of this VLAN.
The screenshot below shows what I have after adding both VLANs:
Jul 28, 2014 Chinnari Pellikuthuru 28 July 2014 Episode 1000 BY Bharath G IN Chinnari Pellikuthuru Telugu Daily Serial All Episodes No comments Chinnari Pellikuthuru Daily Serial - Today's Episode 1000 telecast in Maa TV on July 28 2014. Sep 28, 2018 chinnari pelli kuthuru serial, chinnari pellikuthuru, chinnari pellikuthuru serial full story, chinnari pellikuthuru serial watch online, chinnari pellikuthuru todays episode Advertisement Categories: Chinnari Pellikuthuru, Daily Serials, Daily Soaps, MAA, MAA Serials, TV. Jul 30, 2014 Gemini tv Chinnari Pelli kuthuru Daily serial. BEST POP SONGS WORLD 2018 (ED SHEERAN CHARLIE PUTH BRUNO MARS) THE BEST SPOTIFY PLAYLIST - LIVE 24/7 Magic Box 450 watching Live now. Youtube chinnari pellikuthuru latest episode. Chinnari Pellikuthuru Daily Serial today episode. Chinnari Pellikuthuru cast and crew. All telugu daily serials online. All Maa TV Serials and Daily Serials. Watch Online Sasural Simar Ka TV Show Episodes on Colors Channel on Thursday 13th July. Sasural Simar Ka TV Show Online, Sasural Simar Ka TV Show Time, Sasural Simar. May 15, 2012 'Balika Vadhu', the popular show on Colors TV, reach a milestone on Monday and has managed to withstand the test of time for over four years. The serial complete 1,000 episodes on.
The next thing we need to do is assign interfaces to the VLANs we created. To do this, we will go back to the Interface assignments tab, as shown below:
Notice that there is now a field showing Available network ports. In our case, we will first replace le0 currently assigned to LAN with “VLAN 10 on le0” and click on Save.
Now we will create another interface for the DMZ that will be assigned to VLAN 20. To do this, we select “VLAN 20 on le0” and click on the add selected interface button.
Notice that it automatically added an interface called “OPT1” and the number keeps increasing as you add more interfaces, i.e., OPT2, OPT3, etc. To edit this interface, we will just click on the interface name.
By default, the new interface is not enabled and clicking the “Enable Interface” checkbox brings up a host of options, including changing the interface name and specifying an IP address. The settings on my own interface are as shown below:
When you are done with your configuration, Save and Apply the Changes.
By default, the DHCP server is turned off on new interfaces so, if you want to use DHCP, you need to enable and configure it. In this lab, devices in the DMZ will have their IP address settings manually configured.
Furthermore, there are no firewall rules on new interfaces by default, as shown below:
This means that all packets through/to this interface will be denied. For testing purposes, let’s add a rule that allows ICMP from any source to any destination.
This ends the configuration on pfSense although you may need to restart pfSense for the configuration changes to take effect.
The next thing we need to do is configure the switch to which pfSense is connected. In our GNS3 lab, I will add a router with a switch module (NM-16ESW) and our lab setup now looks like this:
The configuration on the switch-router is as follows:
Pfsense Install Guide
To test our lab setup, I will use DHCP for PC1 but will assign a static IP address to PC2:
Now let’s try to ping between PC1 and PC2:
Great! We have connectivity.
Summary
Let’s end this article here, where we have seen how to configure VLANs on pfSense and make it act as a router on a stick. We have also seen firewall rules briefly in this article but, in the next article, we will look more deeply into firewall rules.
I hope you have found this article insightful and I look forward to writing the next one in the series.
How To Install Switch Network
References and Further Reading
- Configuring VLANs on pfSense: https://www.highlnk.com/2014/06/configuring-vlans-on-pfsense/
- Firewall Rule Basics: https://doc.pfsense.org/index.php/Firewall_Rule_Basics